This guide contains information on detecting fraudulent online communications, mitigating the damage of a successful phishing or spam attack, and preventing future security breaches.
What is Phishing?
Phishing is the fraudulent attempt to obtain sensitive information, or data, such as usernames, passwords and credit card details by disguising oneself as a trustworthy entity in an electronic communication. Typically carried out by email spoofing or instant messaging, phishing often directs users to enter personal information at a fake website which matches the look and feel of the legitimate site. (Wikipedia)
Spam and Phishing attacks are the most common security concern that you will encounter in daily operations. While UVM does employ email filters to help mitigate this issue, it is important to be able to identify and protect yourself from online fraud.
Examples of Phishing Attempts
These are some common examples of phishing or spam attempts. If you see a communication that looks like these, please take extra precaution.
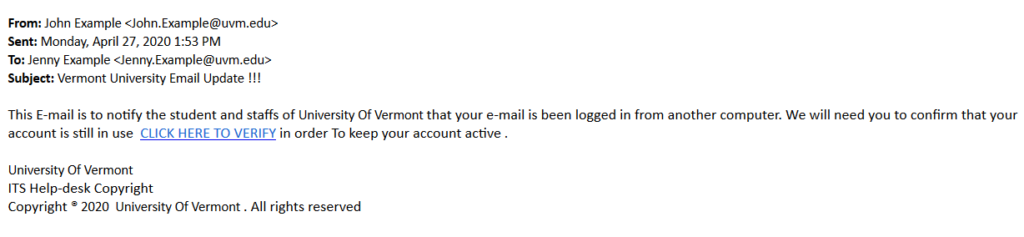
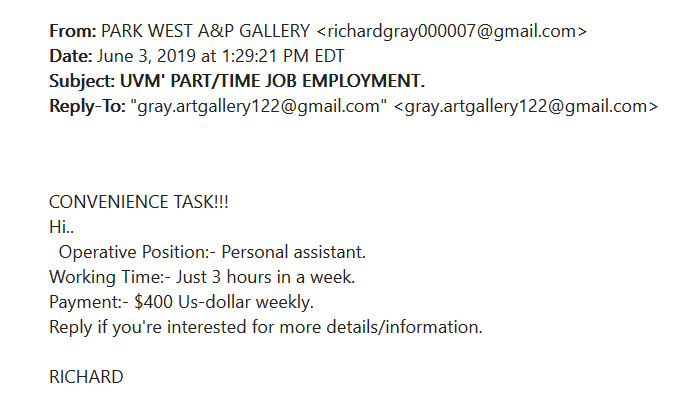
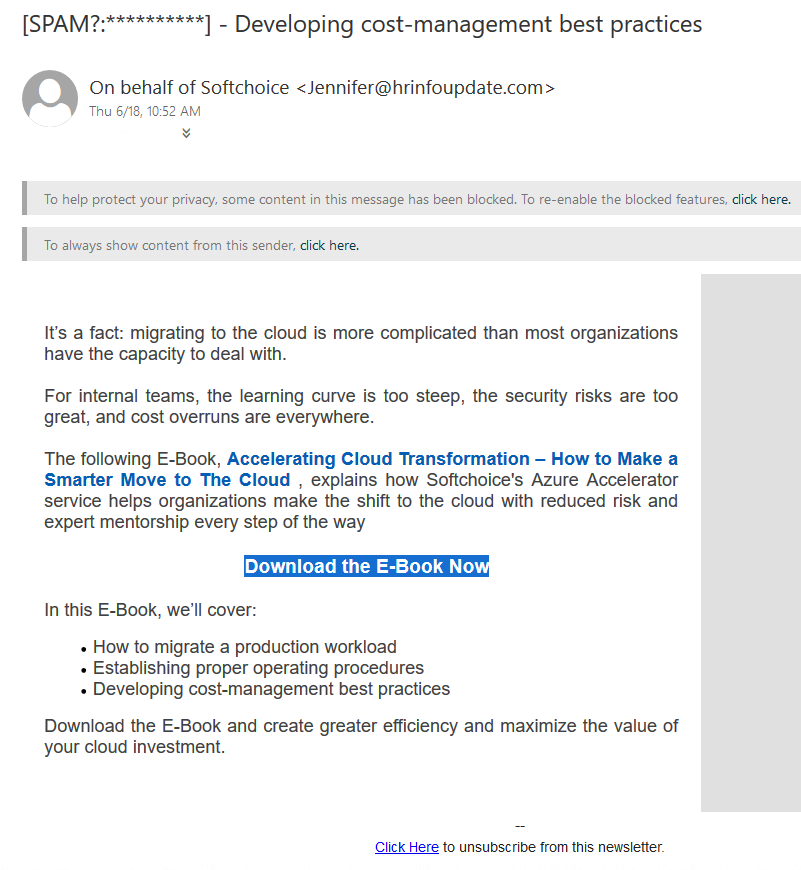
Potential Consequences
The consequences of a successful phishing attack can vary greatly in severity – from only requiring a password change, to requiring that you contact your bank to cancel credit cards or a governmental institution in the case of a stolen Social Security Number.
Phishing attacks are a serious threat to the individual and to our institution. They are regularly successful in stealing information from politicians and other important figures, along with causing grave breaches in organizations like hospitals.
For some context on how serious the results of an attack like this can be, see the following articles:
- MalwareBytes Blog: “Sophisticated phishing: a roundup of noteworthy campaigns”
- Business Insider: “Hillary Clinton’s campaign got hacked by falling for the oldest trick in the book”
- Zix.com: “12 Email Security Incidents Involving U.S. Education Institutions”
Identifying and Reporting a Phishing Attempt
Check for Common Red Flags
The following are some common indicators that an email is not legitimate. The presence of these warning signs does not guarantee that an email is fraudulent, but you should exercise caution when you see them.
| Red Flag Type | Example | Why it’s suspicious |
|---|---|---|
| Fake FROM Address | An email sent from “someone@uvm-edu.com” | Attackers use email addresses that look like they come from inside your organization in an attempt to appear legitimate. Check the FROM address on an email to make sure that it is actually from who it claims. |
| Fake Link Addresses | An email with a link like: http://uvmedu.xyzsites.com/passwordform | This link is meant to look like its destination is a UVM site, but actually links to an unknown page. Real links to UVM sites will always contain “uvm.edu” and should start with “https“. |
| Urgent or Threatening Subject Line | Subject: “we have footage of you” | Attackers use scare tactics like claiming to possess compromising photos or personal information in order to extort access or money. These claims are rarely true, and are just meant to scare the recipient into complying. |
| Misspellings and Improper Grammar | An email containing the sentence: “I installed mine malwareo nto your device” | This is a common tactic used by attackers when sending mass emails. “Mistakes” like this help ensure that only people more likely to fall for their scam respond to the initial email. |
| Demanding or Asking For Money | An email claiming to possess footage of you and containing demands like: “If you wish to destroy the videotape- transfer me 319 euro in Bitcoins” | Legitimate emails will never ask for money like this, and a scammer’s claims to possess incriminating materials are highly unlikely to be true. |
| Suspicious Attachments | An email from someone you don’t know with an attachment like “financial_report.pdf” or “holidayVacation.exe” | Certain file types, like PDF files, videos, and even Word documents, can contain hidden programs which can be used to steal your information and control your computer. Other potentially dangerous files, like EXE files, can be disguised by giving them a misleading name. Never open attachments from someone you do not trust. |
| Offers that are “Too Good To Be True” | An email containing an offer like this: “We wish to congratulate you for being the winner of 650,000.00 USD in the recent Publishers Clearing House E- mail Lottery.Kindly send your contacts to lottowinoffice@null.net” | Scammers use offers like this to trick recipients into giving out private information like bank details or contact information. |
| Asking For A Password | An unexpected email asking for your password or providing a reset link. | You will never be asked to send your password in a legitimate email. If a link asks you to sign in or enter other information, make sure that the URL looks correct. |
Ask the Tech Team
If you are unsure whether a specific email is fraudulent, please feel free to contact the Help Line for us to take a look: https://www.uvm.edu/it/kb/contact/
Report Possible Phishing Attempts
Incoming email at UVM goes through Proofpoint, an anti-spam, anti-malware, and anti-phishing service. If you receive email that appears to be malicious, but was not tagged by Proofpoint, please forward full mail headers to abuse@uvm.edu.
You may also contact the UVM Tech Team who may work with our Systems Administrators to address this issue.
View Additional Online Resources
The following online resources contain more information on detecting spam and protecting yourself from future attacks.
- FTC: How to Recognize and Avoid Phishing Scams
- Phishing Quiz: Test Your Spam Identification Skills
- Wikipedia: Phishing
- Have I Been Pwned?: Check for compromised accounts
What To Do if You’ve Been Compromised
Change your Passwords
When one of your accounts becomes compromised, it’s possible that other accounts you own may have been compromised as well. This is especially true when you use the same password for multiple sites or have an account under the same email address on many sites.
After one of your accounts is compromised, the safest thing to do is change passwords for all your other accounts. While this is likely to be a difficult task, it may be useful to focus on certain types of account for extra precaution, such as:
- School and Work Accounts (UVM)
- Change your NetID password at https://account.uvm.edu/change-password
- Bank and Credit Accounts
- Social Media (Facebook, LinkedIn, etc.)
- Shopping (Amazon, Ebay, etc.)
These sites contain sensitive data and extra care should be taken with potential compromised credentials.
Monitor your Accounts
If you think someone may have gained access to an account of yours, be on the lookout for suspicious activities that you did not perform:
- Unfamiliar Purchases or Charges (Shopping Sites or Credit Cards)
- Strange Messages to Friends or other Acquaintances (Social Media or Email)
If you see suspicious activity on your UVM account, change your password immediately. If you encounter suspicious activities on another account, change your password and contact that organization immediately. This is especially important for things like credit cards and bank accounts.
If you think someone may have your Social Security Number or other sensitive information, see these pages from the FTC for help with preventing and recovering from identity theft:
Managing your Online Safety
Below are some methods and precautions to help you to protect yourself from spam and phishing attacks online.
Proofpoint Spam Filtering
UVM’s email server uses Proofpoint to filter spam messages from your inbox. Emails that the program thinks are spam will be marked in the subject line with something like “[SPAM – DEFINITE]” or “[SPAM?:****]”.
Please see our dedicated guide on the Proofpoint Spam filter for more information.
Passwords
If you are worried that someone may have gained access to any of your online accounts, it is strongly encouraged that you change the password for that account immediately.
Click here to change your UVM password.
You can also help to protect your accounts by using strong passwords. Strong passwords are usually made up of a combination of different types of characters, like numbers, lower and uppercase letters, and punctuation.
The most important measure of a strong password however, is length.
For this reason, UVM requires passwords to be at least 12 characters long and contain at least two character types. It is strongly recommended that you use the same level of precaution when creating passwords for other sites. You should not reuse passwords.
Helpful Programs
There are several freely available programs that can help you protect yourself from Spam and Phishing attacks, and help to mitigate the consequences of a successful attack.
| Program Name | Purpose | Download Page |
|---|---|---|
| Malwarebytes Anti-Malware | Scans your computer for malicious programs and helps to remove any found. Cost: Free (with premium option) | https://www.malwarebytes.com/ |
| Ad-Blockers (Browser Extensions) | Remove advertisements from websites you visit. Web advertisements can often contain scams and malware. Please note that some sites will ask you to disable these extensions. | Where to find extensions for each major browser: Google Chrome Mozilla Firefox Apple Safari Microsoft Edge |
Keeping Up To Date
Another important method for maintaining your computer’s security is keeping it fully updated when possible. Official instructions for running updates on each major operating system can be found at these links:
Computers managed by UVM also have software that is capable of installing updates or applications.
- Windows: Software Center – SCCM
- macOS: Managed Software Center